Acts of unlawful interference (AUI), attempted thefts carried out with safety violations can give rise to emergency situations with the loss of human life, large financial damage and halt production.
Operational disorder or work interruptions could result in the loss of economic management at the municipal or regional levels as well as in a significant decrease of the population life safety.
Regulations on the use of safety equipment at the sites of FEC (Fuel and Energy Complex) are defined in subordinate acts of the Federal Law N 256-FZ of 21 July 2011 “On safety at the sites of Fuel and Energy Complex”.
Entrance to the sites is by identification card. Visitors’ access except on the grounds is prohibited.
Transport infrastructure’s focus is always associated with high-risk. The threat of terrorism has particularly increased in recent years. Therefore, immediate trustworthy information acquisition about the slightest violations of the security regime has become particularly important in preventing acts of unlawful interference.
The main conceptual requirement for a modern security system is the enforcement of the balance between security and passenger comfort.
Banks carry out cash transactions, storage, transportation and cash collection. Protection of ATMs and cash-in-transit guards from criminal offence is a critical problem of the bank security.
There is a strong probability of group disorderly behavior and the occurrence of mass riots during football games.
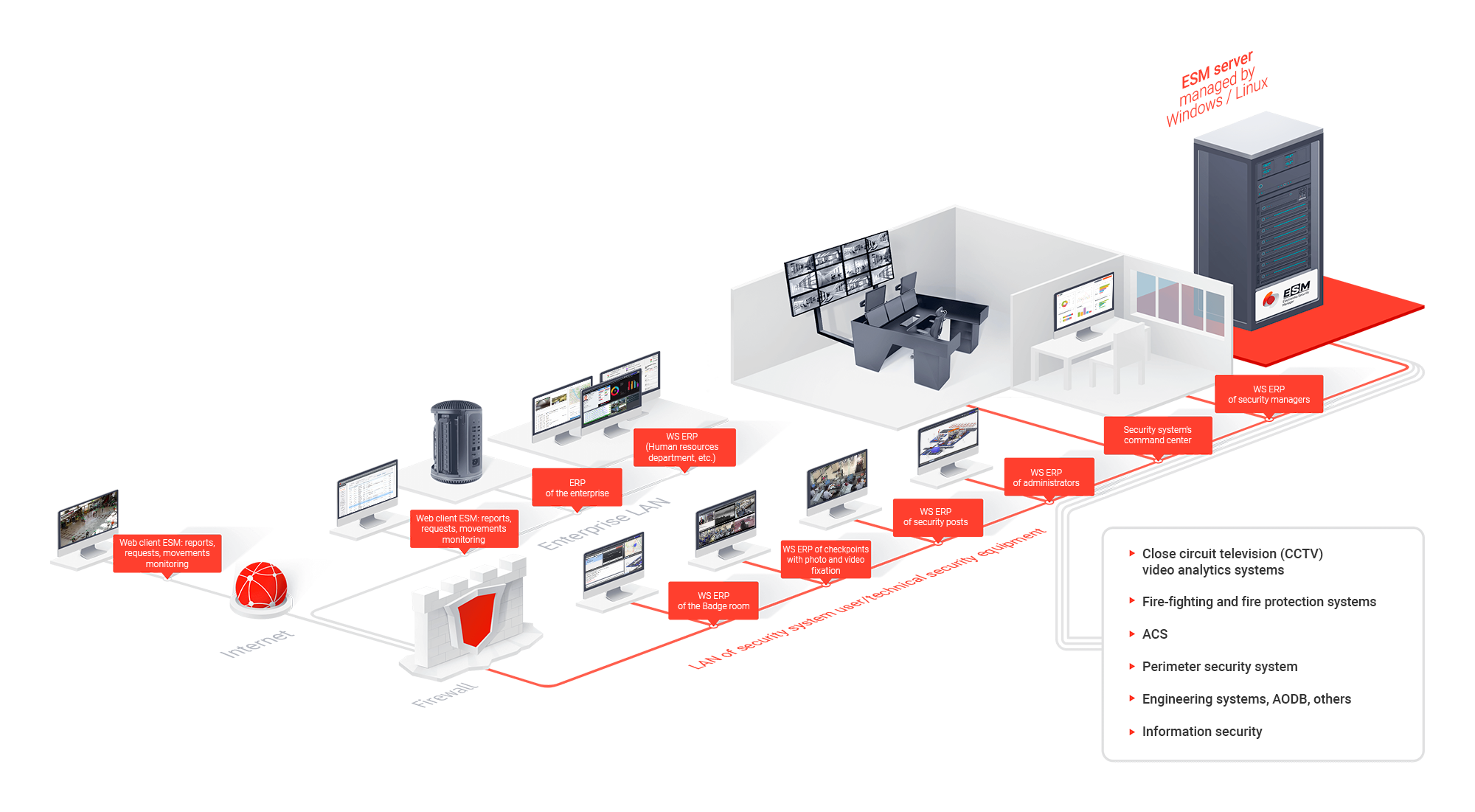
The following secure subsystems are integrated into the hardware-software solution by the principle of “one-stop shop”: access control systems, videosurveillance systems, systems for protecting the perimeter, intruder detection and alarm systems, secure lighting and others.
- Perimeter breach.
- Unauthorized individuals’ entry into the territory.
- Unauthorized presence of vehicles and people in access-controlled areas.
- Terrorism.
- Thefts of material assets, expensive equipment, fuel.
- Violation of work discipline (which may lead to non-performance of job functions)
- Accidents related to violations of the technological process, safety.
- Violation of the vehicle movement plan on the territory of the enterprise (unloading/loading).
- Inefficient use of resources (electricity, water, gas, etc.).
- Entering the building in order to gain access to computers, servers or network equipment.
- The development of safety management systems for large and medium-sized enterprises in fuel and energy sector, transport infrastructure, offices and manufactures, both public and commercial.
- The creation of hierarchical and distributed security systems, from local to federal scale.
- A single center of technical security equipment (TSE) monitoring.
- Perimeter.
- Parking lot.
- Office space, checkpoint.
- Counter hall.
- Points of entrance for visitors.
- Security and anti-terrorist protection of the facility.
- Improving the automation and the efficiency of the security service to prevent attempts to steal inventory.
- Preventing the possibility of the technical process’s disruption.
- Improving the level of the staff’s labor discipline.
- A safety management system that ensures data integration, efficient event processing and alarm signals’ timely transmission to security personnel and management;
- Individual security systems’ level:
-
Access control systems;
-
Perimeter protection systems;
-
Videosurveillance and video analysis systems;
-
Heat monitoring systems;
-
Radar and optical systems;
-
Facility-based and radio contact alert systems;
-
Global positioning systems (based on GPS / GLONASS) and position finding of moving objects;
-
Specialized applications for managers, where the information filtered by various criteria is transmitted (for example, signals about critical deviations in the work of a particular site, claiming direct intervention of the manager).
-